A site I am managing recently came nder a massive DDOS attack from around the globe.
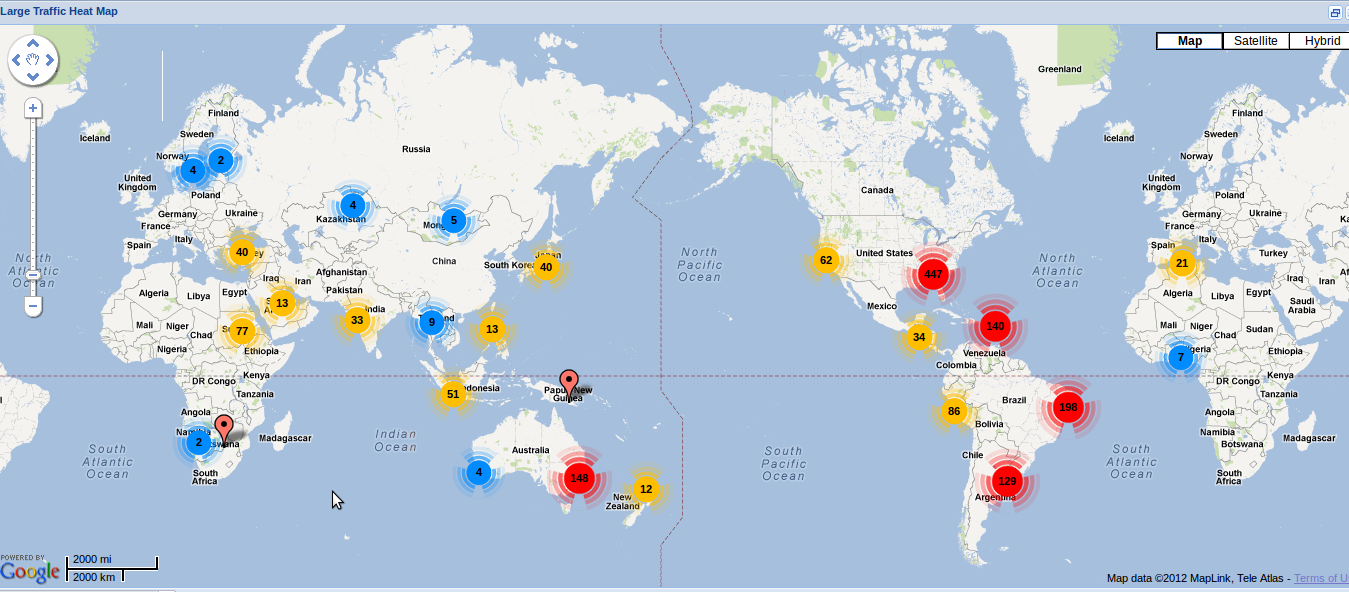
To limit the attack, I used fail2ban to setup a ban system to help mitigate the issue.
Note that this will not stop the attack in its track, but will free up enough resources for your site to continue.
Firstly you need to install fail2ban on your server, using your usual package manager.
Next edit the file /etc/fail2ban/jail.conf and add the following to the end:
[http-get-dos]
enabled = true
port = http,https
filter = http-get-dos
logpath = /var/log/httpd/yoursite-access_log
maxretry = 50
findtime = 300
bantime = 6000
action = iptables[name=HTTP, port=http, protocol=tcp]
iptables[name=HTTPS, port=https, protocol=tcp]
sendmail-whois-withline[name=httpd-get-dos, dest=yourname@yourdomain, logpath=/var/log/httpd/yoursite-access_log]
The above sets fail2ban to scan your access logs, and will ban any ip that accesses more than 50 requests in 300 seconds.
Adjust to your needs, and also specify your correct path to the access logs, and your email
next create the file filter file: /etc/fail2ban/filter.d/http-get-dos.conf
and puthe the contents as:
# Fail2Ban configuration file
#
# Author: http://www.go2linux.org
#
[Definition]
# Option: failregex
# Note: This regex will match any GET entry in your logs, so basically all valid and not valid entries are a match.
# You should set up in the jail.conf file, the maxretry and findtime carefully in order to avoid false positives.
failregex = ^<HOST> -.*\"(GET|POST).*
# Option: ignoreregex
# Notes.: regex to ignore. If this regex matches, the line is ignored.
# Values: TEXT
#
ignoreregex = ^<HOST> -.*\"(GET|POST).*Googlebot
The above will scan your logs , and if it has more than 50 requests in 300 seconds, it will be banned.
Add to the exclude regex any line you do not want banned. Here I placed google.
Next create a new action.
I copied the standard sendmail-whois.conf to sendmail-whois-withlines.conf, and added some code to display the offending lines in the email.
This helps to debug, and confirm the ip was rightly banned.
The part I changed was actionban as such:
actionban = printf %%b "Subject: [Fail2Ban] <name>: banned <ip>
From: Fail2Ban <<sender>>
To: <dest>\n
Hi,\n
The IP <ip> has just been banned by Fail2Ban after
<failures> attempts against <name>.\n\n
Lines containing IP:<ip> in <logpath>\n
`grep '\<<ip>\>' <logpath>`\n\n
Here are more information about <ip>:\n
`/usr/bin/whois <ip>`\n
Regards,\n
Fail2Ban" | /usr/sbin/sendmail -f <sender> <dest>
Using this I managed to get the site up, but it is not the only defense, and should not be yours.
Once I managed to get the site back up, a 3rd part service from dosarrest was installed, to limit these attacks.
My log file shows:
fail2ban.actions: WARNING [http-get-dos] Unban 200.89.152.218
fail2ban.actions: WARNING [http-get-dos] Ban 114.159.55.102
fail2ban.actions: WARNING [http-get-dos] Unban 201.79.109.137
fail2ban.actions: WARNING [http-get-dos] Ban 186.232.112.66
fail2ban.actions: WARNING [http-get-dos] Ban 186.52.1.28
fail2ban.actions: WARNING [http-get-dos] Unban 201.29.152.45
fail2ban.actions: WARNING [http-get-dos] Unban 69.31.51.70
fail2ban.actions: WARNING [http-get-dos] Unban 200.106.47.206
fail2ban.actions: WARNING [http-get-dos] Ban 190.40.28.79
fail2ban.actions: WARNING [http-get-dos] Unban 186.115.231.194
fail2ban.actions: WARNING [http-get-dos] Ban 69.31.51.70
fail2ban.actions: WARNING [http-get-dos] Unban 177.40.93.175
fail2ban.actions: WARNING [http-get-dos] Ban 186.115.231.194
